As interconnectivity between people and objects becomes more commonplace, adding connectivity, or “smart” technology, to all facets daily life will become the new standard.
This new technology has been dubbed the Internet of Everything (IoE), or the Internet of Things (IoT). The phrase was coined in 2009 by British technologist Kevin Ashton while working at Auto-ID labs, a research group he founded at the Massachusetts Institute of Technology (MIT) that focuses on networked radio-frequency identification (RFID) technology.
IoT can be described as data-driven interactions from person to machine (P2M), machine to machine (M2M) or person to person (P2P).
Early forms of the IoT included digital tags of non-connected objects. For example, by attaching unique barcodes, quick response (QR) codes and RFID chips to objects that are not “smart” (such as books, merchandise and information kiosks), these objects can then be tracked by Internet-enabled devices and networks. However, this form of IoT requires humans to interact directly with tagged objects by using a network-enabled device.

Modern incarnations of IoT involve direct communication between “smart” objects. Objects that were previously not “smart,” like household appliances, can now become part of household networks via WiFi. Additionally, these objects may be able to function as designed without direct input by humans.
By making objects “smart,” or Internet-enabled, automation between devices can be streamlined. The number of connected devices will only continue to grow. According to Gartner, Inc., by 2020, IoT will grow to 26 billion connected devices from 900 million in 2009.
Additionally, according to a 2012 Forrester Consulting survey, 43 percent of firms have already have an IoT solution, or plan to have an IoT solution in place, within a year. It can be easy to see that many companies see IoT as the future of technology.
Consumer Application
After smart phones, the second most commonplace smart devices widely available to consumers are televisions. Smart TVs allow users to connect their TVs to the Internet to access apps and video content. Instead of connecting “smart’ technology to a TV, such as video-on demand (VOD) via a cable box, the TV itself has become smart by allowing connections to existing VOD applications and services.
However, the growth of IoT is not simply in the realm of smart TVs. Other Internet-enabled home appliances include refrigerators, ovens, thermostats, door locks, fire detectors, slow cookers and even toothbrushes.
The explosion of applications for IoT is becoming lucrative enough that Google Inc., recently acquired IoT device maker, Nest, in the hopes of monetizing and integrating technology into home appliances.

IoT applications of appliances include smart thermostats and air conditioners (such as those made by Nest) that use cloud computing and data processing to automatically regulate heat and energy usage in a home. Other applications include the integration of existing P2M technologies. For example, a smart phone app can be used to remotely unlock an Internet-enabled door, or to pre-heat a network-enabled oven.
The future of IoT has captured the imaginations and minds of designers, technologists and electronics manufacturers so much so that at the yearly Consumer Electronics Show in January 2014, French IoT company Sense was honored at the convention’s Innovations Design and Engineering Awards. The Sense Mother is an IoT hub that contains sensors called Mother Cookies. These cookies are small enough to be attached to any object or person in a home and can be used to track temperatures, lighting and even proper pill intake. The hub tracks the movement of the cookies to ensure designated tasks and parameters are met. This kind of IoT hopes to use data-driven stats and information to improve wellbeing and security in one’s home for day-to-day use.

Other applications include using personal information generated from IoT devices to directly advertise to consumers. For example, an Internet-enabled refrigerator may read the contents of your fridge to recommend a product that paid for advertising with the fridge manufacturer. The combinations of using various tagged devices are endless for customer, advertisers and manufacturers.
Security and Privacy
As the connectivity of devices in daily life increases, so do concerns over privacy and network security.
Two Black Hat presentations in August 2013 brought attention to vulnerabilities that exist in common IoT devices. The presentations focused on exploits and security holes in smart TVs. Citing infrequent firmware and software updates, the presenters discussed the vulnerability of personal information in connected apps like Netflix, Hulu and Pandora. The presenters even discussed the possibility of remote takeovers of TVs. The presenters, SeungJin Lee and Professor Seungjoo Kim, explained that all Internet-enabled devices are as vulnerable to attackers and coordinated attacks as personal computers.
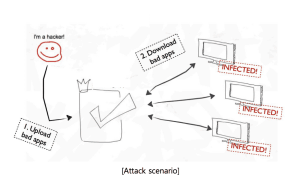
As users begin to add more IoT devices into their daily lives, the risks will only increase. Non-digital natives may not have the skills or knowledge required to update every device in a home IoT network. Insecure passwords in connected apps could also mean loss of secure banking and credit card information.
Other concerns of IoT involve the use of private information and data. Many consumers are unaware of how their private data will be used by companies. As IoT becomes more commonplace, users must know how companies will use their data.
Recent revelations from Target, Neiman-Marcus, Edward Snowden and the National Security Agency (NSA) have made personal security an important political and social flashpoint in the United States. Increasingly, users want to know how their data will be used and maintained by companies.
Security and privacy will become a paramount concern as consumers add more Internet-enabled devices into their lives.